When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
You might have heard ofProton Mail.
However, this could have been very easily prevented exactly by the incriminated user.
The suspect willingly decided to add the optional recovery email: anAppleiCloudaddress.
Subsequently, the Big Tech giant ultimately discolsed identifying information connected to this account to law enforcement.
Privacy vs anonymity
Let’s start with the obvious elephant in the room.
Privacy and anonymity are two very different things and they are not interchangeable.
Most importantly, privacy and anonymity are distinctive concepts by law.
Privacy is mostly recognized as a human right.

Whilst, anonymity simply isn’t.
As we have seen, mixing up these two definitions can be costly.
This is also true for all your stored messages.
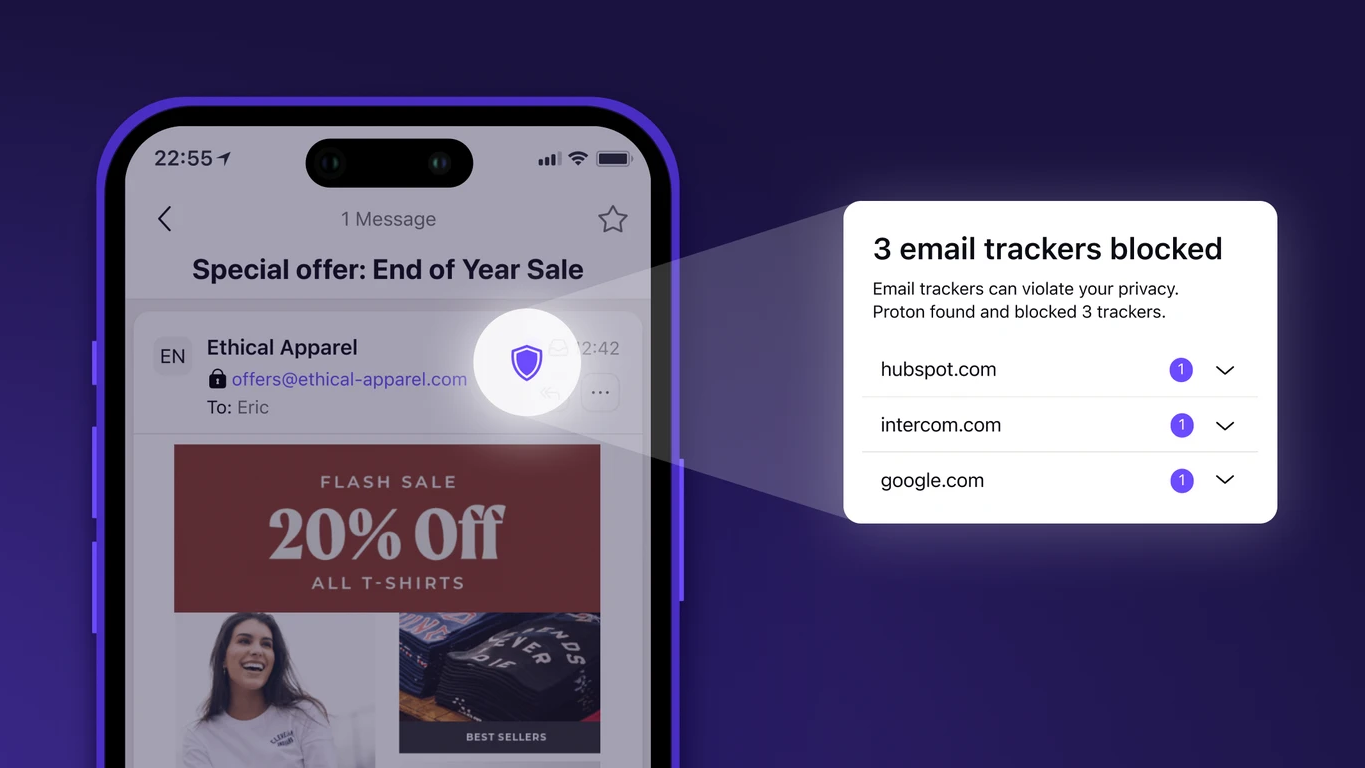
Other advanced privacy features includeunique email aliasesand atracker blocker.
However, the provider still has access tosomeidentifiable information.
Law enforcement can force companies to hand these details over as part of ongoing investigations.
In 2023 alone, the company received 6,378 legal orders.
The team successfully contested 407 of them, but it had to comply with 5,971. https://t.co/sxGfCaAwIyMay 8, 2024
1.
I advise creating alternative accounts or using burner phone numbers instead, for an extra layer of anonymity.
Proton Mail, for instance, accepts Bitcoin and even cash.
Again, the user could have easily prevented this from happening.
Our top recommendation at the time of writing isNordVPN.
However, Tor uses a so-called Onion routing system.
Using Proton Mail over Tor brings several advantages.
Proton offersan Onion sitethat you might use to access all its security products, Proton Mail included.
We test and review VPN services in the context of legal recreational uses.
Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.